We will explain how this new trick works and what you should do to avoid falling into the trap of fraudsters.
Years of cryptocurrency through zoom
The stratag used for the theft of Kryptos is generally based on a combination of social engineering and smart technical element. It all begins when the account of already hacked victims writes acquaintances. This is how Crooks gives confidence in their goals because contact is not a foreigner.
Then the victim is offered to continue communicating to the zoom. The pretexts may vary. For example, fraudsters can complain about the poor quality of communication on a telegram or other sending messages that they originally came into contact with the aim.
Thus fraud follow the following process:
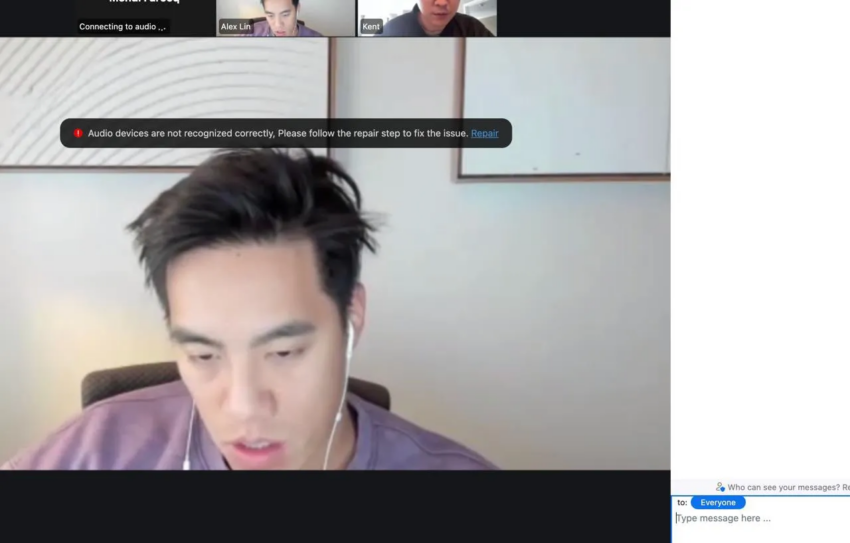
- Platform usurp. Instead of a actual link to the zoom, the URL is sent to a clone page that opens directly in the browser. A picture of the AI generated knowledge can be broadcast using a video.
- Technical problems. A picture generated by AI can begin to complain about technical problems such as the absence of sound. To assume a problem, the victim is asked to download the zoom_sdk_support file. In fact, it is offered to download a harmful program to steal its cryptocurrencies.
- The malicious program is in the system. The infected file downloads the program details necessary for flight and approach the start -UP sentences and portfolio cookies.
Judging by network reports, fraudsters most often use this diagram and occasionally adjust one of their components.
According to Huntress, eight binary files have been detected on the infected Mac, from a false software to update the telegram to the stolen door, allowing the remote controls to be operated.
Online, victims say they have lost most of their savings because of this trick.
In addition, users who have trapped say that attackers remain in contact with themselves after they have stolen crypto to ridicule them.
In addition, victims of this stratag are not only individual users but also the whole society. The case of funds of this type is well known to the Hypersphere capital fund.
Who is the source of these attacks?
Although experts are not yet able to agree on those responsible for these attacks. The following organizations could involve:
- Blluenoroff / Ta444: Lazarus Group’s daughter cell specializing in cryptocurrency theft.
- SNE AND SCAMQUERTEO: Russian teams that sell the funds of the fund.
| Our recommendations | Why is this important? |
|---|---|
| Check the domain. You must make sure you are well invited to approach and not on the false platform related to it. | False URL addresses are often masked as a subdomain. |
| Never install “correction” sets during a call. If someone tries to persuade you to install software immediately, ignore their request. | Real Zoom only performs updates via the customer. |
| Keep a separate environment. A normal browser for e -maly and calls, different environment for work with wallets; It is best to have a separate computer. | Reduces the risk of cross -fly cookies and triggered sentences. |
| Keep your cryptocurrencies in your wallets for cooling. So fraudsters will not have access to your assets. | Although the operating system is at risk, the attacker will not sign the transaction. |
| Use two -Factor verification applications. | Reduces the risk of hacking that begins with phishing. |
While the investigation continues in this case fraud, the platforms and portfolio suppliers are recommended to carefully monitor the connection of the account and cancel any suspicious access to access.
Morality History: The less physical are funds, the more easy it is to fly.
Notification of irresponsibility
Notice of non -response: In accordance with the TRUST project, Beincrypto undertakes to provide impartial and transparent information. The aim of this article is to provide accurate and relevant information. However, we invite readers to verify their own facts and consult a professional before it decides on the basis of this content.

